Guide
System Architecture: Tutorial & Best Practices
Table of Contents
System architecture is the high-level conceptual structure of a software system, defining its essence, organization, and operations. It specifies interactions between system components to ensure reliable data transmission and processing and to align system behavior with business goals.
System architecture can take various forms, from detailed architecture diagrams to more high-level blueprints. Ultimately, system architecture guides everything from component selection to interface design. Each system architecture decision can profoundly impact a system's performance and design.
There are rarely one-size-fits-all answers regarding system architecture. When designing complex systems, architecture decisions are not binary, and architects must consider a variety of tradeoffs to find effective solutions given business requirements. This article will help teams make quality system architecture decisions by exploring system architecture in depth, including system architecture components, types, and best practices.
Summary of key system architecture concepts
The table below summarizes three system architecture concepts this article will explore in detail.
| Concept | Description |
|---|---|
| Components of a system architecture | System architecture encompasses all aspects of a system, such as software, hardware, data, interfaces, communication protocols, third-party services/APIs, user interactions, and security layers. |
| Types of system architecture | Monolithic, microservices, event-driven, serverless, edge computing, and peer-to-peer are common system architecture types. |
| System architecture best practices | Best practices for system architecture include:
|
Components of a system architecture
System architecture is the high-level blueprint of a software system and all its major components and interactions. It encompasses all aspects of the system (e.g., software, hardware, data, interfaces, communication protocols, third-party services/APIs, user interactions, and security layers) to ensure that they work together effectively and efficiently to achieve specific goals.
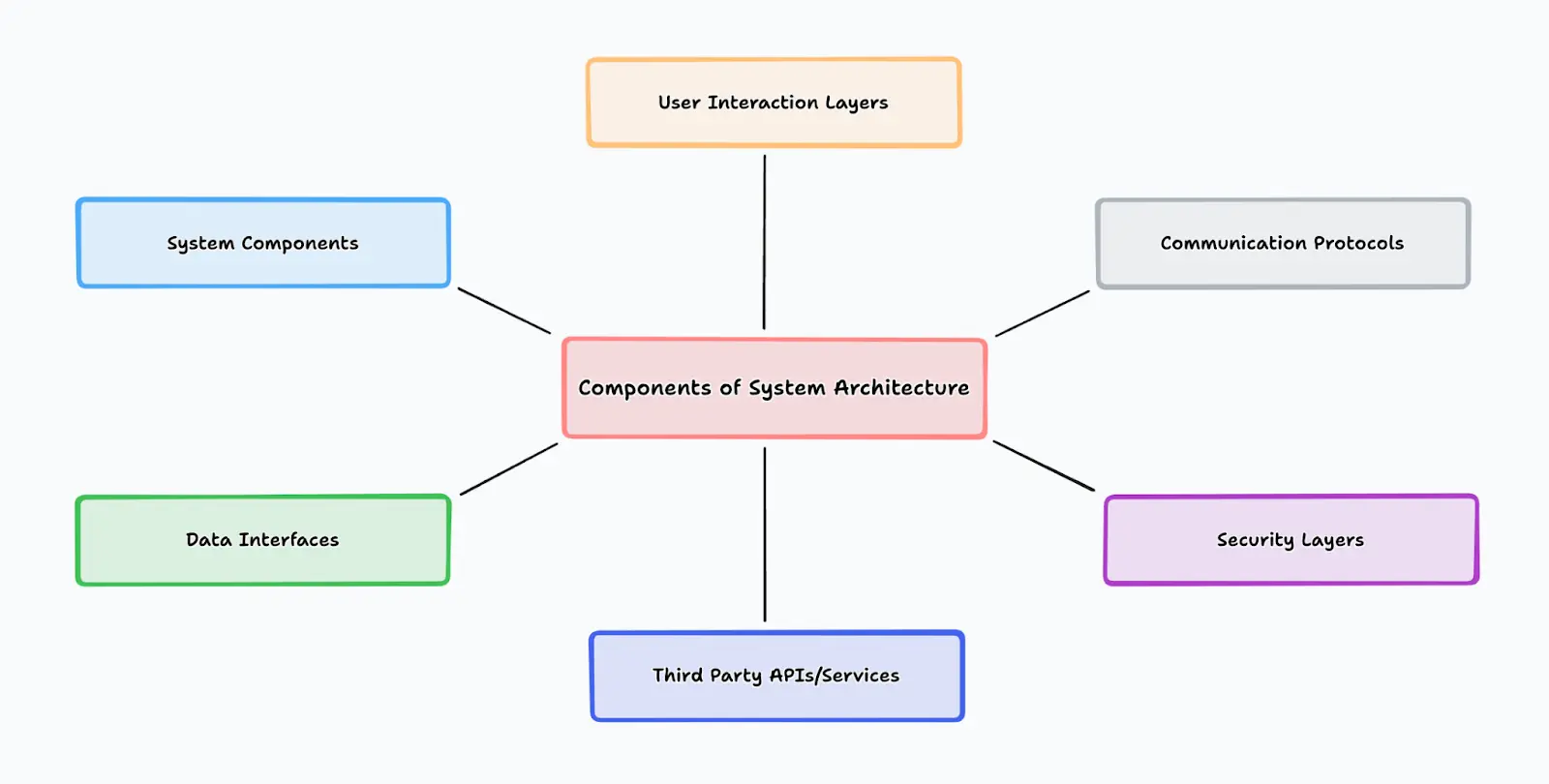
The graphic above shows six common components of system architecture, from user interaction layers to data interfaces. The sections that follow discuss each of these components in greater depth.
System components
A system is comprised of various software and hardware components. Hardware encompasses tangible elements like servers, storage devices, and networking equipment. Software components include the application itself, libraries, databases, and the operating system upon which application code runs. Together, system components collaborate to execute tasks, manage resources, and provide interfaces for user interaction.
Data interfaces
Data interfaces define how data is stored, retrieved, and manipulated. This includes storage mechanisms (e.g., relational databases, NoSQL databases), access patterns (e.g., sequential access, random access), and strategies for optimizing data retrieval and management.
Communication protocols and interfaces
Components within a system rarely operate in isolation. Communication protocols and interfaces establish how they interact and exchange data. These protocols define the language and structure for data exchange, ensuring seamless communication across different components.
Third-party services and APIs
Modern systems often leverage external functionalities offered by third-party services. APIs (Application Programming Interfaces) act as intermediaries, enabling communication and data exchange between the system and these external services, expanding system capabilities without duplicating development efforts.
User interaction layers
User interaction layers define how users interact with the system. They encompass the user interface (UI)–the visual elements for user interaction–and the user experience (UX)–the overall system experience. These layers strive to create an intuitive and user-friendly environment for end users.
Security layers
Security layers implement measures like user authentication (verifying user identity), authorization (controlling access to resources), and data encryption (securing data during storage and transmission) to safeguard the system from unauthorized access, breaches, and other threats.
Six types of system architecture
System architecture styles dictate how multiple components within a system interact and communicate. Understanding these styles empowers developers and architects to select a strategy that aligns best with their project's needs and goals. In this section, we briefly examine some modern system architecture styles. For a more in-depth look into the advantages and considerations of each style, check out our free guide.
Monolithic architecture
In a monolithic architecture, the entire application is deployed either on a single server or across multiple servers with load balancers within a distributed system. In either case, the application functions as a single unit. This approach simplifies development, offers faster execution, and eases testing and deployment processes.
However, monolithic architectures also have limitations. For example, monolithic applications face scalability challenges, as it is difficult to scale only one part of the application in isolation. This often leads to inefficient use of resources and higher deployment costs. In addition, maintaining a large, monolithic codebase becomes cumbersome, and adopting new technologies can take time and effort. Finally, deploying changes in a monolithic architecture often requires maintenance or downtime, impacting user experience.

Diagram of a monolithic architecture. (adapted from Source)
Full-stack session recording
Learn moreMicroservices architecture
Microservices architectures break systems down into independent, business-focused services. This structure boasts scalability, flexibility, and resilience. Teams can scale individual services to meet specific demands, and independent development and deployment cycles accelerate time-to-market. Microservices also isolate failures, preventing system-wide outages.
However, this approach introduces complexity in managing service discovery, communication, and data. Distributed system challenges like latency and data consistency require careful design and robust tooling to ensure smooth operation and reliable communication across services.
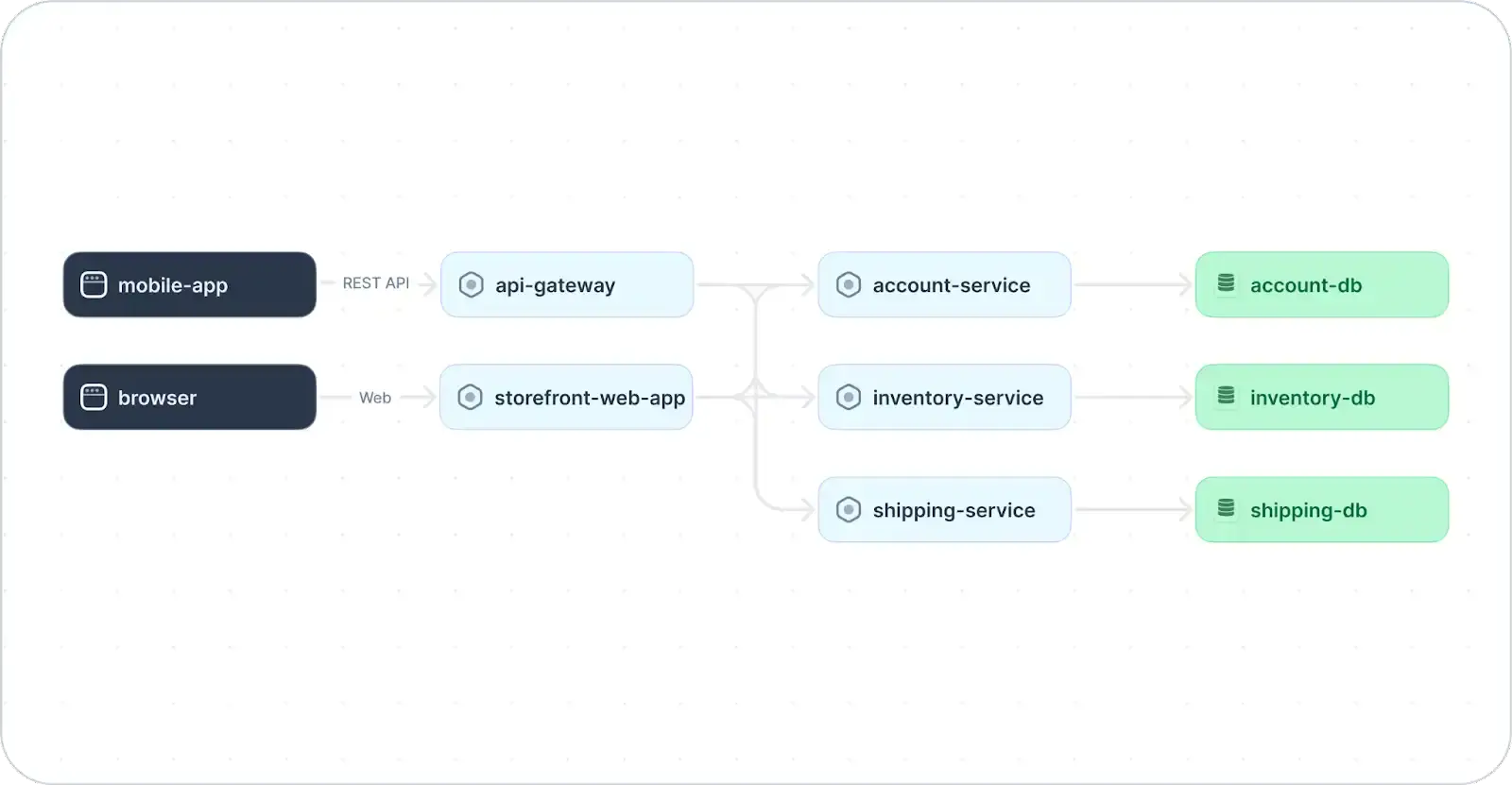
Diagram of a microservices architecture. (adapted from Source)
Event-driven architecture
Event-driven architectures decouple components through asynchronous event exchange. This promotes scalability, flexibility, and fault tolerance with isolation as services react to events independently.
However, this approach introduces complexity in managing event flows, eventual consistency, and message ordering. Event-driven systems may experience temporary inconsistencies until events propagate, and special mechanisms are needed to ensure messages are delivered in the proper sequence when message order is crucial. Debugging event-driven systems can also be challenging due to their reliance on asynchronous communication.
Despite these considerations, event-driven architectures offer significant advantages for building loosely coupled, scalable, and resilient systems.
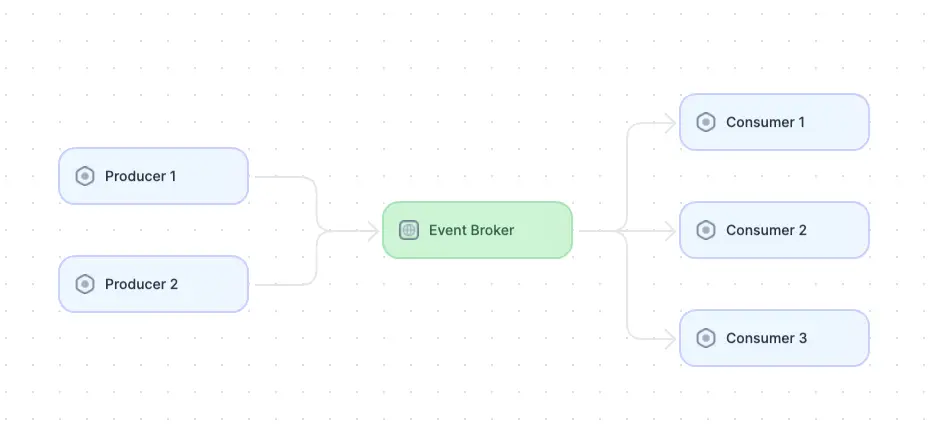
Diagram of an event-driven architecture. (adapted from Source)
Serverless architecture
Serverless architectures empower developers to focus on code, not servers. They build functions triggered by events and deploy them on a cloud provider's platform. These platforms automatically scale and manage infrastructure, which offers significant advantages as applications grow. Serverless applications benefit from seamless scaling, pay-per-use cost efficiency, and faster deployment cycles.
However, serverless comes with several challenges, including:
- Vendor lock-in
- Potential cold start latency
- Limitations in execution environments
- Complexities in monitoring and debugging
Despite these considerations, serverless architectures offer an attractive development approach for building scalable and cost-effective applications.
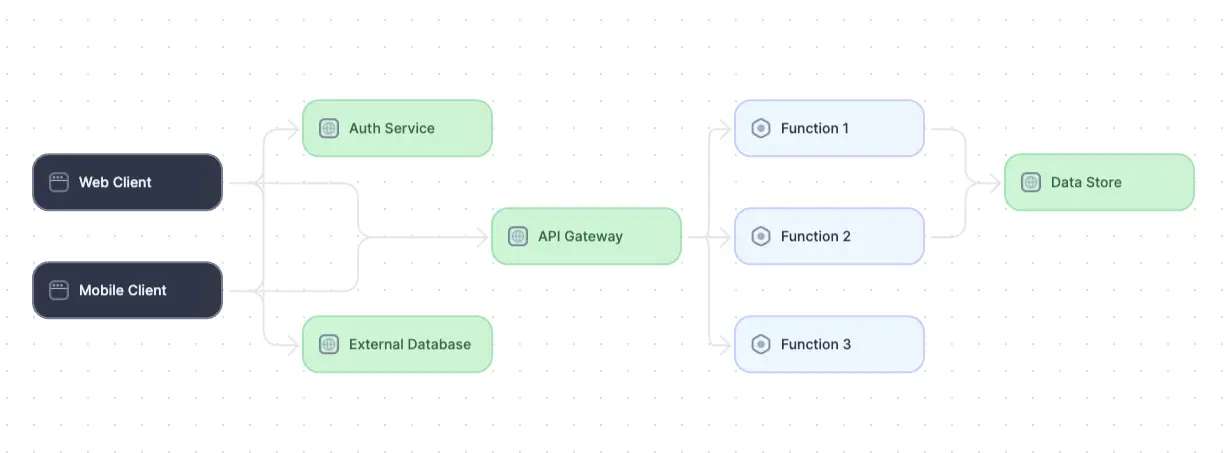
Diagram of a serverless architecture. (adapted from Source)
Edge computing architecture
Edge computing pushes processing power to the network's edge, closer to devices and users. This minimizes latency, optimizes bandwidth usage, and improves application reliability. Data processing and storage occur locally, reducing reliance on centralized cloud servers.
However, managing this distributed infrastructure requires careful consideration of resource constraints, network connectivity, and security risks. Designing efficient applications and robust security measures are crucial for successful edge deployments.
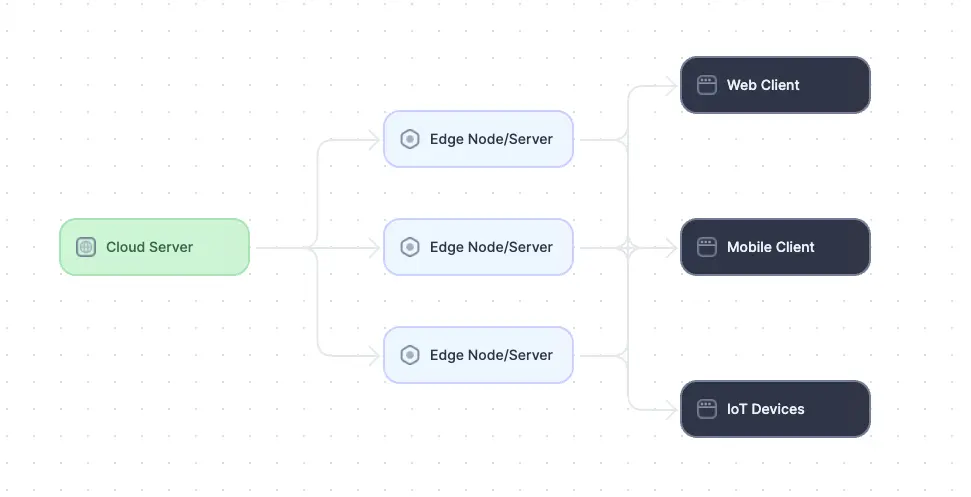
Diagram of an edge-computing architecture. (adapted from Source)
Interact with full-stack session recordings to appreciate how they can help with debugging
EXPLORE THE SANDBOX(NO FORMS)
Peer-to-peer architecture
Peer-to-peer architecture distributes control and resources across participating devices, eliminating central servers. This structure boasts scalability, resilience, and efficient resource utilization. By adding more nodes, the network dynamically scales to handle fluctuating workloads.
However, challenges arise in managing network overhead, data consistency, and security risks. Peer-to-peer networks require careful design to ensure optimal performance and reliable communication across a potentially large and dynamic network.
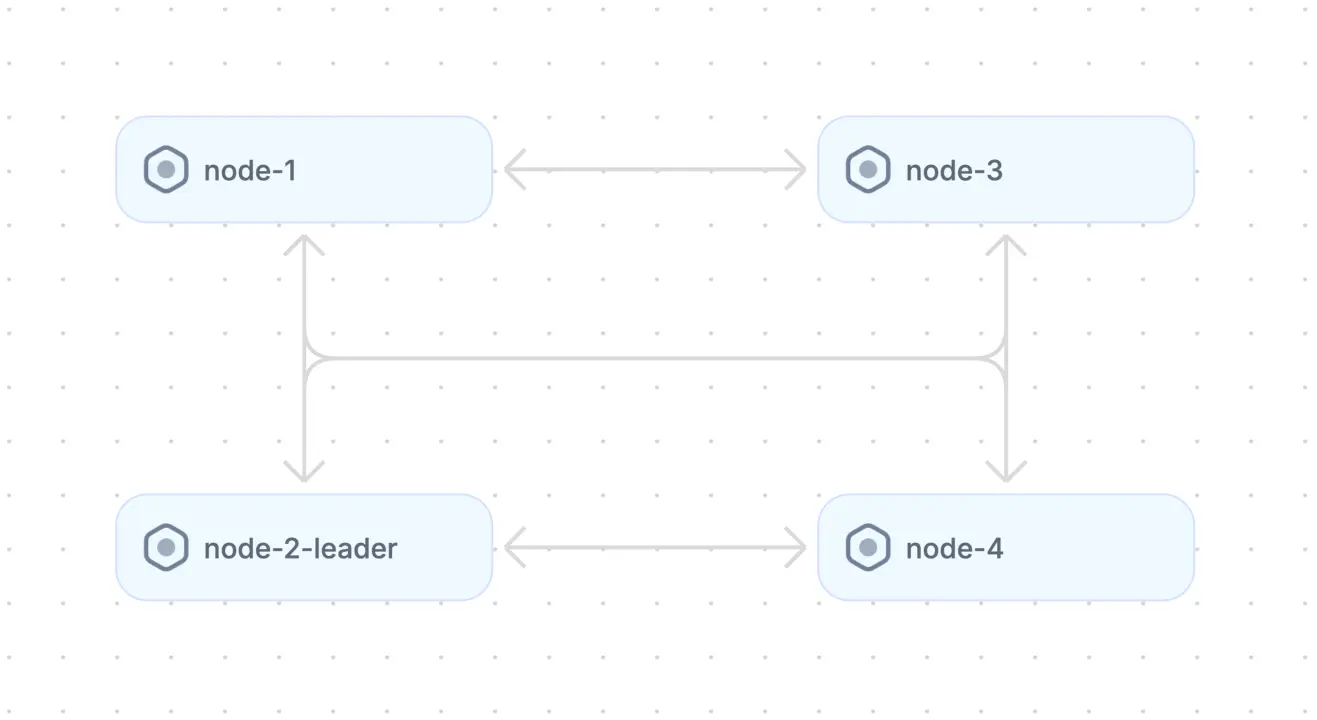
Diagram of peer-to-peer architecture. (adapted from Source)
Five essential system architecture best practices
The following sections present five system architecture best practices to help developers and architects design robust, scalable, and maintainable systems. These best practices encompass the technical considerations and the creation of clear and comprehensive documentation. Let's explore these best practices in more detail.
Embrace architecture as a shared responsibility
Traditional system architecture design practices often rely on designated architects shouldering the entire responsibility. However, an alternative approach involves engaging developers and business stakeholders from the early design stages. This approach offers two significant advantages.
- Increased collaboration - By involving more stakeholders in the design process, architecture becomes a collaborative effort. The architecture benefits from diverse perspectives, such as developers' practical experience and business representatives' strategic vision.
- Better knowledge sharing - Early developer involvement also fosters a deeper understanding of the system and leads to higher buy-in. This benefit is enhanced when documentation is stored in a central, easily accessible location. This centralized access to architectural artifacts ensures transparency and empowers all parties to contribute to the system's evolution.
In practice, earlier engagement from different stakeholders means actively seeking developer input during decision-making, integrating experienced developers into the design process, and ensuring all architectural documents are readily accessible to developers, architects, and business stakeholders. This fosters a collaborative environment where all parties work together to create a robust and well-understood system architecture.
Manage technical debt effectively
Software development accumulates debt–both architectural and technical. Technical debt reflects the gap between the source code's current state and best practices. Shortcuts, hacks, errors, and poor practices contribute to this debt, negatively impacting code quality, performance, reliability, security, and testability.
On the other hand, architectural debt is the divergence between an application's current state and its desired architecture. It stems from design choices, requirement shifts, external dependencies, or legacy systems. Architectural debt issues can hinder alignment with business goals, compliance, integration, and future-proofing.
Here are some practices that can help manage both kinds of debt:
Identifying system architecture tech debt
To uncover hidden system architecture costs:
- Visualize your system architecture in its entirety, including all components and interdependencies.
- Assess your architecture and code against desired outcomes, best practices, and stakeholder expectations.
- Leverage tools like architecture reviews, code reviews, metrics, benchmarks, and stakeholder feedback to pinpoint areas of concern.
- Document these debt items, their causes, and potential consequences for clear communication and prioritization.
Prioritizing system architecture tech debt
Not all debt is equally urgent. Prioritize architectural and technical debt based on their impact on development efforts and business goals. Utilize frameworks like cost-of-delay to sort debt into critical, high, medium, or low categories. Analyze each debt item's dependencies, tradeoffs, and potential opportunities to inform your plan.
Repaying system architecture tech debt
Develop a structured and iterative approach to address accumulated debt. This might involve refactoring, redesigning, rewriting, upgrading, or replacing components. Align these activities with project goals, scope, budget, and timeline. Open communication with stakeholders, team members, and users throughout the process is crucial.
Preventing system architecture tech debt
Adopt a proactive and disciplined approach to prevent future debt. Before implementing a new system or feature in code, make sure your team has conducted sufficient upfront system design to prevent the need for major architectural rework later. In addition, ensure there is an established process for collaborative and continuous system design reviews to proactively identify areas for improvement. Finally, maintain comprehensive and up-to-date documentation on system design to facilitate better knowledge sharing and empower all team members to contribute to the project.
One click. Full-stack visibility. All the data you need correlated in one session
RECORD A SESSION FOR FREEDocument system architecture
Documenting and communicating a system architecture can be challenging. System architecture documentation should explicitly capture architectural requirements, decisions, and tradeoffs, ensuring clear communication and informed decision-making throughout the project lifecycle. While traditional written documentation is vital in this process, it is equally important to visualize the system's core components using different types of diagrams. The table below describes three common types of architecture diagrams.
| Diagram type | Value provided |
|---|---|
| System architecture diagram | Provides a high-level overview of the entire system architecture, giving stakeholders a clear understanding of the technology landscape. |
| Sequence diagram | Visualizes dynamic processes and workflows within technical systems, enabling stakeholders to see how different components interact. |
| Network diagram | Offers crucial information for troubleshooting, network design, and security analysis, empowering stakeholders to understand the infrastructure behind the networking strategy. |
System architecture, sequence, and network diagrams are powerful tools that can significantly enhance documentation by providing visual representations of system behavior and a targeted focus on key system components. This balances technical detail and business-critical information to foster a shared understanding of the system for all stakeholders.
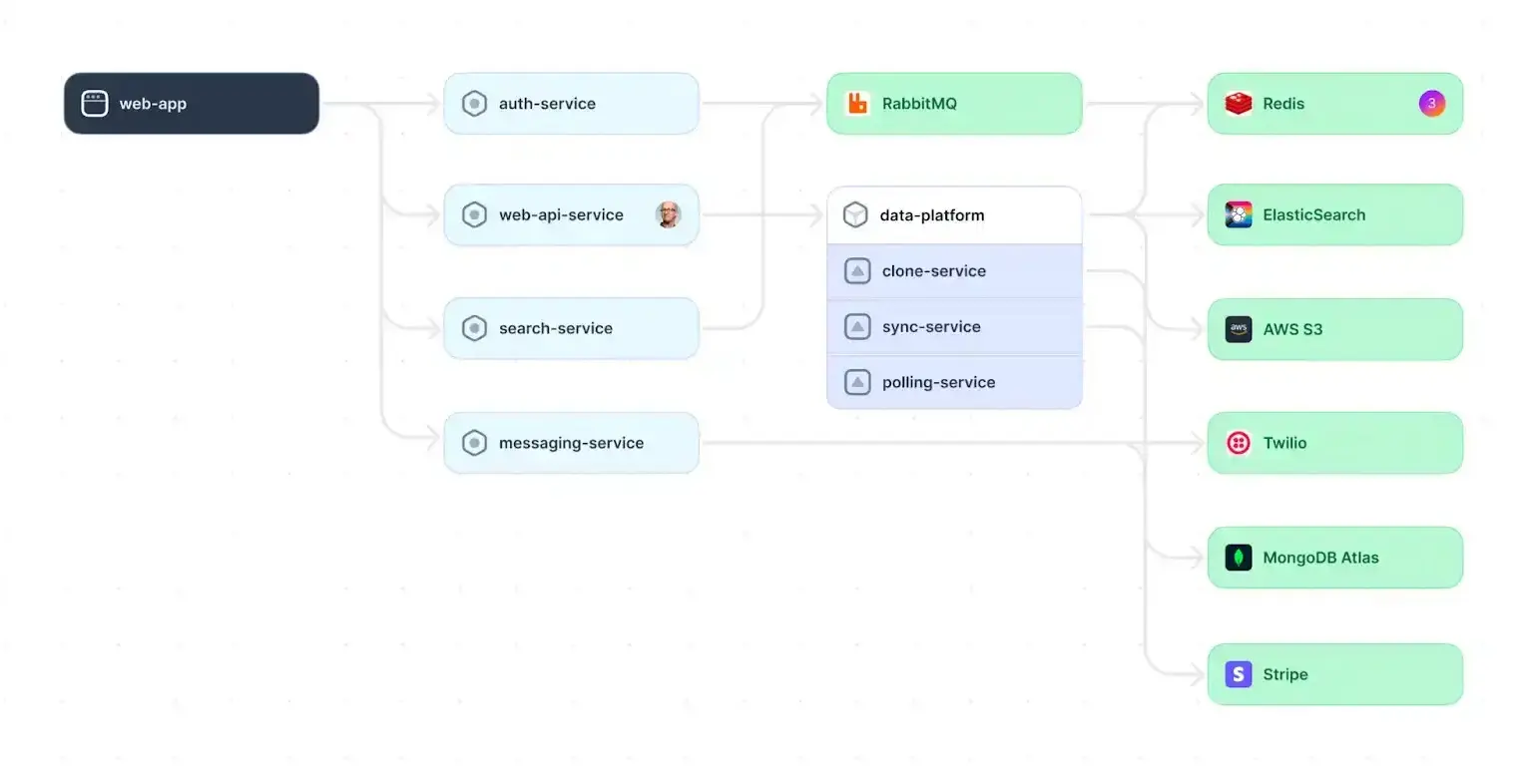
Example of a system architecture diagram
Maintain separation of concerns
A fundamental principle for crafting robust and maintainable system architectures is the concept of separation of concerns. This principle advocates for decomposing the system into well-defined modules with clear boundaries. Each module encapsulates a specific functionality or responsibility, minimizing interdependence with other parts of the system. Here is how the separation of concerns benefits system architecture:
- Enhanced modularity - By separating concerns, each module acts as a self-contained unit with a clear interface. This modularity simplifies development, testing, and maintenance. Modifications within a module have minimal impact on other parts of the system, promoting isolation and reducing the risk of unintended consequences.
- Improved maintainability - Well-defined modules with limited dependencies are easier to understand, modify, and debug. Developers can focus on specific functionalities without getting entangled in complex interactions with other modules. This fosters a more maintainable system architecture that evolves efficiently over time.
- Promotes loose coupling - Modules interact through well-defined interfaces, minimizing direct dependencies on each other's internal implementation details. This loose coupling makes the system more adaptable and resilient to changes. Modifications within a module can be implemented without requiring changes throughout the entire system.
- Facilitates easier testing - By isolating functionalities, developers can focus on testing individual modules in a controlled environment, leading to more efficient and comprehensive testing strategies.
A classic example of separation of concerns is utilizing a microservices architecture. This architectural style decomposes the system into distinct services, each with a specific responsibility or business function.

Example of a microservices architecture (adapted from Source)
A microservices architecture is just one example of how the separation of concerns principle can be applied in system design. By following this principle throughout the system design process, developers can create more easily developed, tested, and maintained systems.
Leverage the right tools
Architecture tools should help your team accomplish two goals:
- They should help architects design performant, resilient, and scalable applications quickly.
- They should empower developers to succeed in their day-to-day work: debugging, making performance improvements, developing new features, and collaborating more effectively.
With these goals in mind, let’s look at some key features to look for when picking a tool for your team.
Architectural observability
Implementing architectural observability equips teams with deep insights into the system's internal behavior and eliminates confusion. This includes monitoring communication patterns to proactively identify and address potential issues. In addition, having a clear and dynamic view of the system's architecture fosters a shared understanding among developers, architects, and stakeholders.
In short, the tool should automatically detect, generate, and document your architecture diagrams and system overviews, keeping them current and updated using real system data.
Automatic drift detection
Any change–intentional or otherwise–can cause a system's architecture to deviate from its documented state. When using traditional, static documentation tools, these changes often go unnoticed or undocumented. However, automatic drift detection identifies these discrepancies promptly, allowing for swift corrective action before issues arise. It directly connects to the system infrastructure, actively listening to the components and dependencies and immediately notifying relevant team members of any changes or discrepancies.
Insights into production behavior
Mapping architectures and dependencies is a useful starting point, but developers still need a way to see how requests actually flow through their production systems. One effective way to accomplish this is to utilize full-stack session recordings, which capture real-world interactions across the frontend, backend, and infrastructure layers.
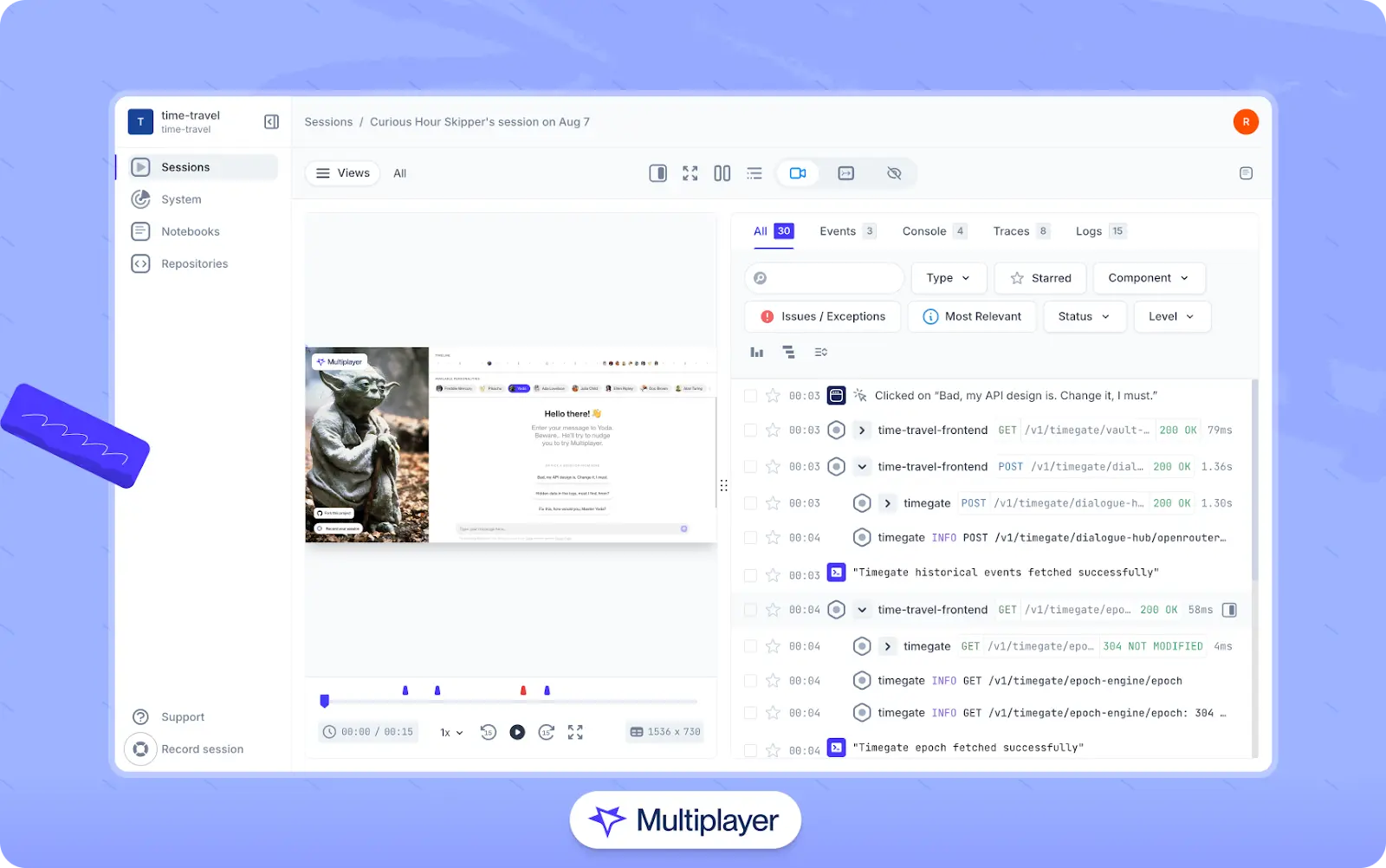
Multiplayer’s full-stack session recordings
Recordings create a living record of user actions, API calls, and system responses that teams can revisit during debugging, performance tuning, or when deciding how to implement new features. Instead of relying on guesswork or fragmented logs, engineers can replay what happened end-to-end. In addition, developers can use the context from session recordings as input to AI coding assistants to give copilots and AI IDEs the context they need to generate accurate fixes, tests, and features with minimal prompting.
Interactive, executable documentation
Collaboration deepens when teams investigate, document, and share findings in a structured and centralized way. However, traditional docs often grow stale quickly, live in disconnected silos, and rarely capture the nuance of why choices were made or how the system actually behaves in practice.
More modern tools allow developers to create interactive notebooks that combine written and executable elements. Using these tools, your team can utilize text blocks for requirements, design decisions, and ADRs; executable code and API blocks to design and test integrations; and full-stack session replays for deeper visibility and live debugging. AI assistance can also generate blocks based on natural language to create documentation more easily.
Stop coaxing your copilot. Feed it correlated session data that’s enriched and AI-ready.
START FOR FREEConclusion
System architecture serves as the blueprint for any software system. By understanding the overall system architecture and system design best practices, developers and architects can make informed decisions that lead to robust, scalable, and maintainable systems.
Following established best practices��–such as embracing a collaborative approach, managing architectural debt effectively, and leveraging the right tools–empowers teams to design, document, and evolve their systems efficiently. By prioritizing clear communication and a shared understanding among stakeholders, architects can ensure that the system architecture aligns with business goals and delivers long-term value.