Guide
SaaS Development: Tutorial & Best Practices
Table of Contents
Software as a Service (SaaS) refers to any software application hosted by a service provider and made available to users over the Internet. The primary goal of SaaS is to allow users to get the business benefits of an application without the overhead that comes with traditional on-premise installations. Instead, the SaaS provider handles all infrastructure, middleware, and data management tasks.
The SaaS approach simplifies user access and allows high scalability, multi-tenant configurations, and efficient resource utilization. It also enables rapid iteration and updates, benefiting users with regular improvements without requiring manual software updates. While SaaS simplifies user experience, this popular cloud service model can complicate application development.
In this article, we explore how to implement SaaS architectures that support robust scalability, security, and fault tolerance through the lens of six best practices. We also discuss strategies for other important considerations like managing multi-tenancy, optimizing resource allocation, and ensuring high availability.
Summary of key SaaS development best practices
The table below summarizes the six best practices we will examine in this article.
| Best practice | Description |
|---|---|
| Ensure application security | Securing SaaS applications requires encrypting sensitive data both in transit and at rest, implementing role-based access control (RBAC), and conducting regular security audits. |
| Build flexible subscription and billing management | Flexible subscription models (monthly, yearly, tiered, etc.), secure payment gateways, automated billing systems, and tracking key metrics are important practices that contribute to better customer management. |
| Design robust APIs | Build APIs that contribute to security and operational efficiency by prioritizing control plane development, isolating tenants at the API level, and building clear interfaces. |
| Plan for scalability | To handle growing demand, use horizontal scaling to add servers or vertical scaling to increase server capacity. If using a cloud provider, configure auto-scaling features to dynamically adjust resources based on real-time traffic. |
| Streamline development and testing | Adopt continuous integration/continuous delivery (CI/CD) pipelines to streamline development and testing, implement automated testing to catch errors before deployment, and roll out new features using A/B testing and feature flags to reduce risk. |
| Employ modularity | Utilize modular architectures and coding practices from the project's outset. As the application grows, consider breaking components into independent services to manage complexity and scalability concerns. |
Understanding SaaS architecture and development
A key consideration in designing a SaaS architecture is providing a unified, seamless, and secure experience for multiple users (or tenants). SaaS architectures rely on strong isolation mechanisms to ensure each tenant’s data and resources remain secure and independent. They strategically partition tenant data and utilize dynamic routing to direct tenant requests to appropriate resources based on tenancy and infrastructure configurations.
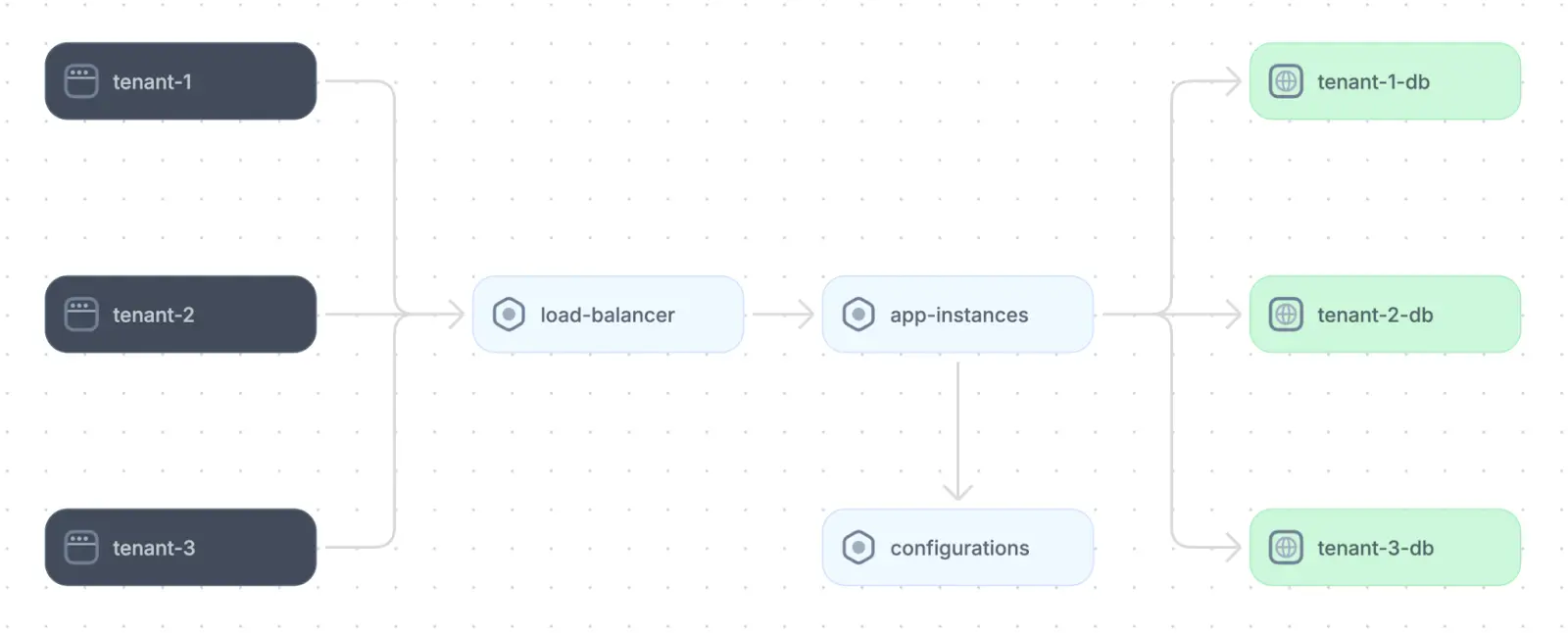
Example of a SaaS application architecture (adapted from source)
SaaS applications also prioritize rapid deployment and update cycles to enable the continuous delivery of new features and incrementally improve the application in response to customer demands and market changes. Because of these goals, developers must keep practices like partitioning data, dynamic routing, and rapid deployment cycles at the forefront of development decisions.
Before examining these practices in greater depth, let’s take a look at three important concepts in SaaS development.
SaaS deployment models
SaaS applications use different models to efficiently allocate or share resources across tenants. Common approaches include full-stack pool (shared resources among tenants) and full-stack silo (dedicated resources for each tenant). It is also possible to use a mixed-mode approach that combines both strategies.
Full-stack pool is a multi-tenancy model in which users share the same instance of the application. It optimizes resource usage by allowing several users to operate in the same environment while maintaining data privacy through logical isolation.
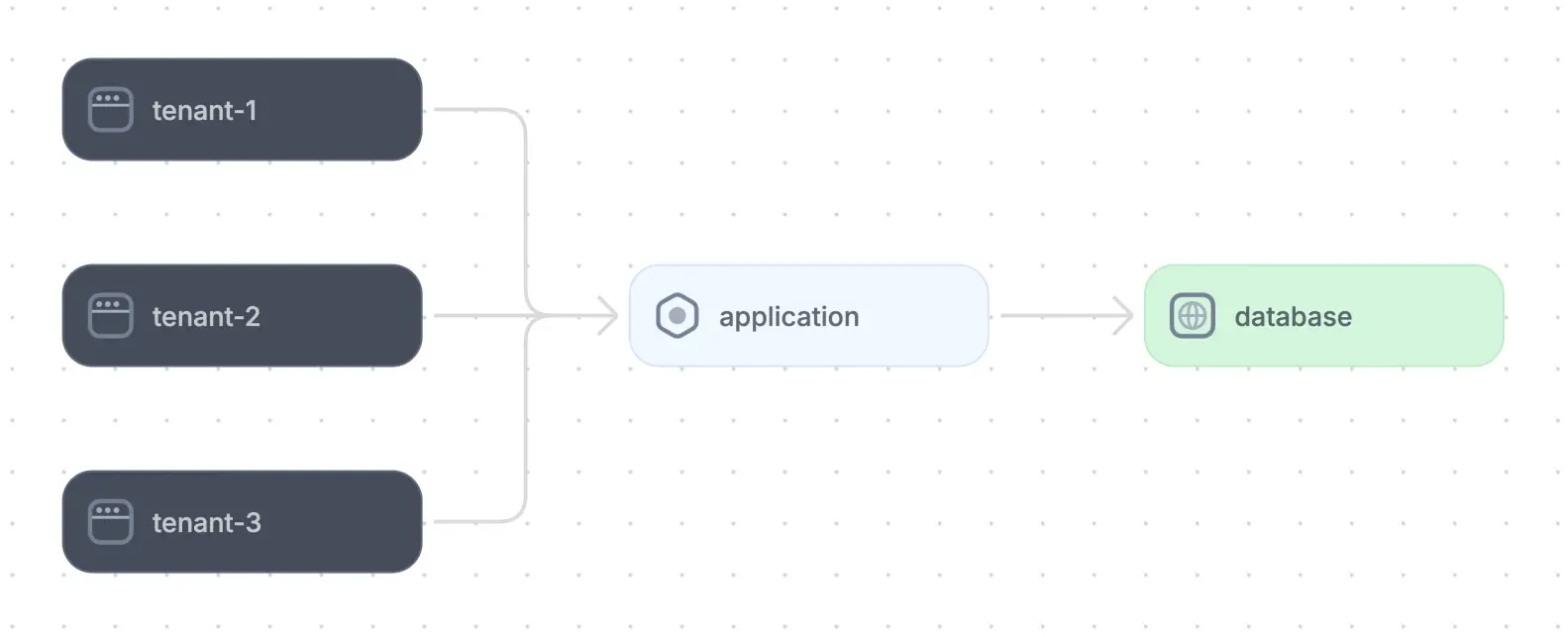
Multi-tenancy model of a SaaS application (adapted from source)
While most SaaS applications are built using a multi-tenant model, it is also possible to create SaaS applications using a full-stack silo (or single-tenant) model. In this model, each user has a dedicated instance of the application, including a dedicated database.
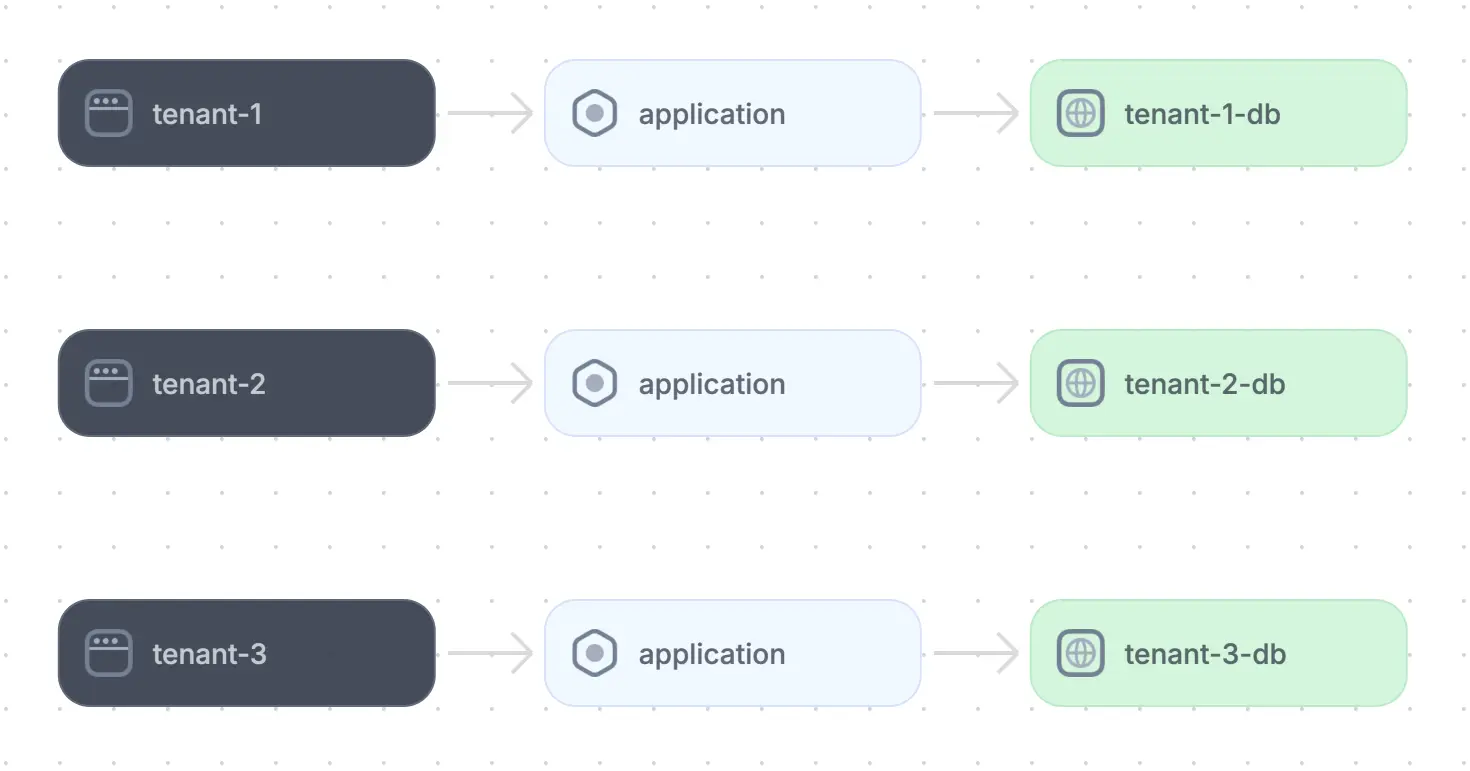
Single-tenancy model of a SaaS application (adapted from source)
The table below summarizes the trade-offs between the multi-tenancy and single-tenancy models.
| Criteria | Multi-tenancy | Single-tenancy |
|---|---|---|
| Cost | Lower cost, as resources are shared among tenants. | Higher cost due to dedicated resources for each tenant. |
| Scalability | High scalability; easier to add new users and scale resources as needed. | Limited scalability; scaling requires additional dedicated resources for each user. |
| Maintenance | Simplified, as updates and maintenance occur centrally. | More complex, as each tenant’s instance requires separate maintenance. |
| Customization | Limited customization, as changes affect all tenants. | High level of customization, as each tenant has their own environment. |
| Data isolation | Logical isolation within a shared infrastructure. | Complete physical or virtual isolation, enhancing data security. |
| Performance | Performance can vary with high tenant activity and may require load balancing to avoid bottlenecks. | Consistent performance unaffected by other tenants’ activity. |
| Compliance & security | Meets general security needs; may face limitations for industries with strict compliance. | Often better suited for strict compliance standards (e.g., HIPAA, GDPR) due to isolated environments. |
| Ideal use cases | Small to mid-sized businesses, startups, and enterprises seeking cost efficiency. | Large enterprises, regulated industries, and organizations require high security and customization. |
As an example, the database platform Oracle offers both single-tenant and multi-tenant options for its SaaS applications. In its single-tenant model, each Oracle database operates independently and requires its own dedicated resources, including memory, processes, and database files. The single-tentant option is generally preferred by industries with strict data security and compliance requirements because it offers enhanced control and privacy.
Oracle introduced a multi-tenant architecture with Oracle Database 12c in 2013. It was designed to coexist with the existing traditional single-tenant architecture. This means that both the multi-tenant and single-tenant architectures can be used in a mixed mode, allowing users to combine the architectures according to their needs.
Control plane vs. application plane
The control plane and the application plane are foundational concepts in system design. While not unique to SaaS, the division of responsibilities between the control and application planes is particularly important in a SaaS architecture.
Control plane
The control plane manages and controls the system’s operation and handles tasks like routing, orchestration, and policy management. It is the backbone of the SaaS environment and is responsible for managing, operating, and analyzing the multi-tenant system. Acting as a centralized hub, it provides global services across all tenants and allows providers to manage the SaaS ecosystem efficiently. Although integral to supporting the tenant ecosystem, the control plane itself is not multi-tenant, as its services apply universally to all tenants. Examples of functionality the control plane handles include identity management, billing, security, and analytics.
Full-stack session recording
Learn moreApplication plane
The application plane handles actual user traffic and executes business functionality, delivering the service directly to each tenant. Unlike the control plane, the application plane is explicitly designed to support multiple tenants, with architecture and deployment models that can vary based on business objectives, domain requirements, and legacy considerations. Each tenant interacts with this plane as an independent user, accessing the service within their unique tenant context. The application plane is responsible for all user-facing functionality, such as processing user requests, handling user-specific data, providing user interfaces, and executing business operations.
Tiering and user roles
Another core offering of many SaaS providers are tiered services, which provide varying levels of features, performance, support, and cost. Implementing tiering in a SaaS architecture affects tenant context, routing, and resource allocation choices.
SaaS platforms typically support various user roles, such as tenant administrators, tenant users, and system administrators. Each role is granted appropriate permissions and access controls to expose relevant functionality while maintaining security and control.
Six critical SaaS development best practices
Now that we have explored key elements of SaaS applications, let’s examine six best practices your team can implement to design them effectively. Implementing these guidelines helps SaaS providers meet evolving customer needs, streamline operations, and deliver reliable, high-performance software at scale.
Ensure application security
Securing user data in SaaS applications requires a focus on encryption, access control, and vulnerability assessments. With these safeguards, SaaS platforms can ensure user data is protected across multi-tenant environments. The following sections explore three essential application security topics.
Data encryption and privacy
Encrypting data both at rest and in transit protects sensitive information across multi-tenant SaaS environments. Encryption algorithms like AES-256 for data at rest and TLS for data in transit create strong security layers and prevent unauthorized access to stored or transmitted data. In addition, some SaaS providers must comply with privacy regulations such as GDPR and HIPAA to ensure that user data is secure and privacy rights are maintained.
Another key practice is to use data masking techniques to obfuscate sensitive information–such as credit card numbers and personal identifiers–in logs, traces, and API responses. This is typically achieved using dedicated tooling or through built-in features of cloud providers. For example, AWS CloudTrail and Azure API Management both offer tools to anonymize and mask data in API logs for better security and adherence to compliance requirements during testing and debugging.
Role-based access control (RBAC)
RBAC minimizes the risk of unauthorized data exposure by limiting resource access to user roles with valid permissions. In a SaaS environment, RBAC serves two important purposes: First, it aligns user roles with employees’ job responsibilities, meaning developers can access only the resources they need for their job duties. Second, RBAC allows fine-grain control over individual client permissions, which allows developers to define and customize roles to meet diverse client needs without altering the core application. This is of particular importance in multi-tenant systems to maintain data privacy between tenants.
Regular security audits & penetration testing
Frequent security audits and penetration testing help identify potential vulnerabilities in SaaS applications before they can be exploited. Tools like Qualys and Nessus enable comprehensive vulnerability scanning, while platforms such as Burp Suite and OWASP ZAP provide thorough penetration testing.
Additionally, bug bounty programs like Bugcrowd and HackerOne incentivize security researchers to identify vulnerabilities that traditional testing may overlook. These platforms connect SaaS providers with a global network of ethical hackers who perform real-world testing on various SaaS components, from APIs to data storage layers. Integrating a bug bounty program helps detect zero-day vulnerabilities and other critical issues proactively. While automated tools perform continuous scans for known vulnerabilities, ethical hackers on bug bounty platforms focus on unique, complex attack vectors.
By adopting a proactive approach with these audits, SaaS providers can stay ahead of emerging threats and continuously improve their security posture, reinforcing the application's resilience against attacks.
Build flexible subscription and billing management
Offering flexible billing models–such as usage-based, subscription-based, or tiered pricing–is a key offering of many SaaS providers because it allows them to cater to customers’ needs. However, supporting flexible building models is not trivial from a development perspective.
Centralizing billing logic
A key step is to manage billing functionalities in the control plane. Doing so centralizes and streamlines operations, enables consistent management across tenants, and provides a single source of truth for billing data.
To decouple billing logic from core application services, many organizations adopt microservices or event-driven architectures with a dedicated service to handle billing needs. In addition, due to its sensitive nature, it is wise to store billing data using a specialized solution and with strict access policies to ensure compliance with legal standards.
Prioritizing transparency
Transparency in billing systems is a customer-centric value that builds trust, improves retention, and ensures compliance with consumer protection laws. Building transparency into a SaaS platform involves a combination of sound internal practices and user-facing features. Consider implementing the steps below.
Internal practices
- Employ metering: Building metering systems for tracking tenant resource consumption (e.g., API requests, storage usage) enables accurate billing based on usage.
- Expose billing events with tenant context: Events related to billable actions should include tenant information and be easily accessible by the billing system, typically through message queues or API calls.
- Conduct thorough auditing and reporting: Maintain detailed billing records and audit trails to support transparency and meet compliance requirements. Regular auditing and comprehensive reporting are essential for accurate billing and regulatory adherence.
User-facing features
- Communicate clearly: Ensure your solution provides tenants with transparent billing information, including detailed pricing structures, usage summaries, and upcoming charges. Build detailed billing dashboards and provide itemized invoices.
- Set up usage alerts and notifications: Implement systems to notify tenants about unusual usage patterns or when they are nearing usage limits. These alerts can help tenants avoid unexpected charges, improving customer satisfaction and reducing billing disputes.
Integrating secure and scalable payment gateways
Integrating trusted and secure payment gateways, such as Stripe, PayPal, or Braintree, is useful for processing transactions while ensuring customer payment data is handled securely. Choose a payment provider that meets PCI DSS (Payment Card Industry Data Security Standard) requirements, protects sensitive card information, and reduces the risk of breaches.
Additionally, scalable payment providers like Stripe support multiple currencies and payment methods, which can expand your application’s accessibility to a global market. This enhances security, boosts customer trust, and provides smoother transactions.
Interact with full-stack session recordings to appreciate how they can help with debugging
EXPLORE THE SANDBOX(NO FORMS)
Tracking and managing subscription metrics
Monitoring essential subscription metrics like monthly recurring revenue (MRR), churn rates, and customer lifetime value (CLV) provides actionable insights into customer behavior, helping businesses make data-driven decisions. Use analytics tools that enable tracking and analyzing these metrics in real time.
For instance, tracking MRR and churn helps gauge customer retention, while monitoring CLV assists in evaluating long-term profitability. This analytics-focused approach to billing can guide product and marketing strategies, making the billing model profitable and customer-oriented.
Design robust APIs
A well-designed API framework enhances a system's functionality, security, and operational efficiency. In SaaS architecture, APIs are particularly important in facilitating separation between the control and application planes and ensuring tenant isolation.
Here are four practices that can help teams design robust APIs:
- Prioritize control plane development: The control plane should be designed to support essential SaaS functions, including onboarding, identity management, metrics collection, billing, and tenant management. As the backbone of a successful SaaS architecture, a comprehensive control plane creates a foundation for consistent operational management.
- Expose control plane functionality through APIs: An API-first approach to the control plane allows all its functionalities to be accessible through well-defined and well-documented APIs. This strategy streamlines automation and external integrations and empowers tenants with self-service capabilities for managing subscriptions.
- Isolate tenants at the API level: APIs should enforce tenant boundaries by validating tenant context in each request. Implement fine-grained authorization within the application plane to ensure each tenant only accesses data and features relevant to their subscription level or permissions.
- Provide clear interfaces: Based on data sensitivity, isolation needs, and the choice of deployment model, different partitioning strategies (e.g., siloed, pooled, hybrid) may be chosen per service. APIs should abstract these data models and provide a uniform data access interface regardless of the underlying data storage method.
Integrating the control and application planes
SaaS architectures require robust communication between the control and application planes to connect their distinct but complementary roles in the overall system. This communication is typically achieved through APIs.
For example, APIs may facilitate onboarding by allowing the control plane's onboarding service to communicate with the application plane to automate the provisioning and configuration of tenant-specific resources. Through APIs, the onboarding service can trigger key actions like setting up user accounts, creating databases, and applying tenant-specific settings.
APIs also enable the application plane to share metrics with the control plane, providing valuable insights into tenant behavior and system performance. This data flow allows the control plane to aggregate metrics that provide customer insights and help teams make informed, data-driven decisions for operational improvements.
Finally, APIs allow the application plane to send billing-related events, including tenant context, to the control plane's billing service. This integration enables accurate bill generation based on tenant activity and resource consumption.
In short, a SaaS application’s successful operation depends on well-defined communication between operational and user-facing functionalities. APIs provide the mechanism for this communication.
The role of documentation
For APIs to be usable, they require comprehensive and well-crafted documentation. Documentation for external APIs should provide key details to allow third-party developers to integrate easily with the SaaS platform’s API. This should include authentication and security details, coding examples, request/response formats, versioning information, possible error codes, and guidance on rate limits, quotas, and best practices for efficient use.
Internal API documentation should include all of the above as well as internal notes, architecture diagrams, and other detailed information to allow developers to understand, use, and maintain the API effectively. This typically involves using a combination of diagramming tools, internal wikis, and API clients like Postman, Bruno, or Insomnia.
The problem with this approach is that each tool only tells part of the story. To gain a holistic view of the system, developers must navigate separate tools, find the relevant information, and piece it together according to the particular issue or user flow they are investigating.
To mitigate these pain points, modern tools like Multiplayer combine different pieces of documentation into a single platform. For example, Multiplayer’s system dashboard automatically discovers a system’s components, APIs, dependencies, and environments, lists them in tabular form, and generates a system map that can be filtered and tailored to different audiences. To document API integrations, Multiplayer notebooks combine enriched text with executable API and code blocks so that developers can document important decisions and share reproducible examples within the same context.
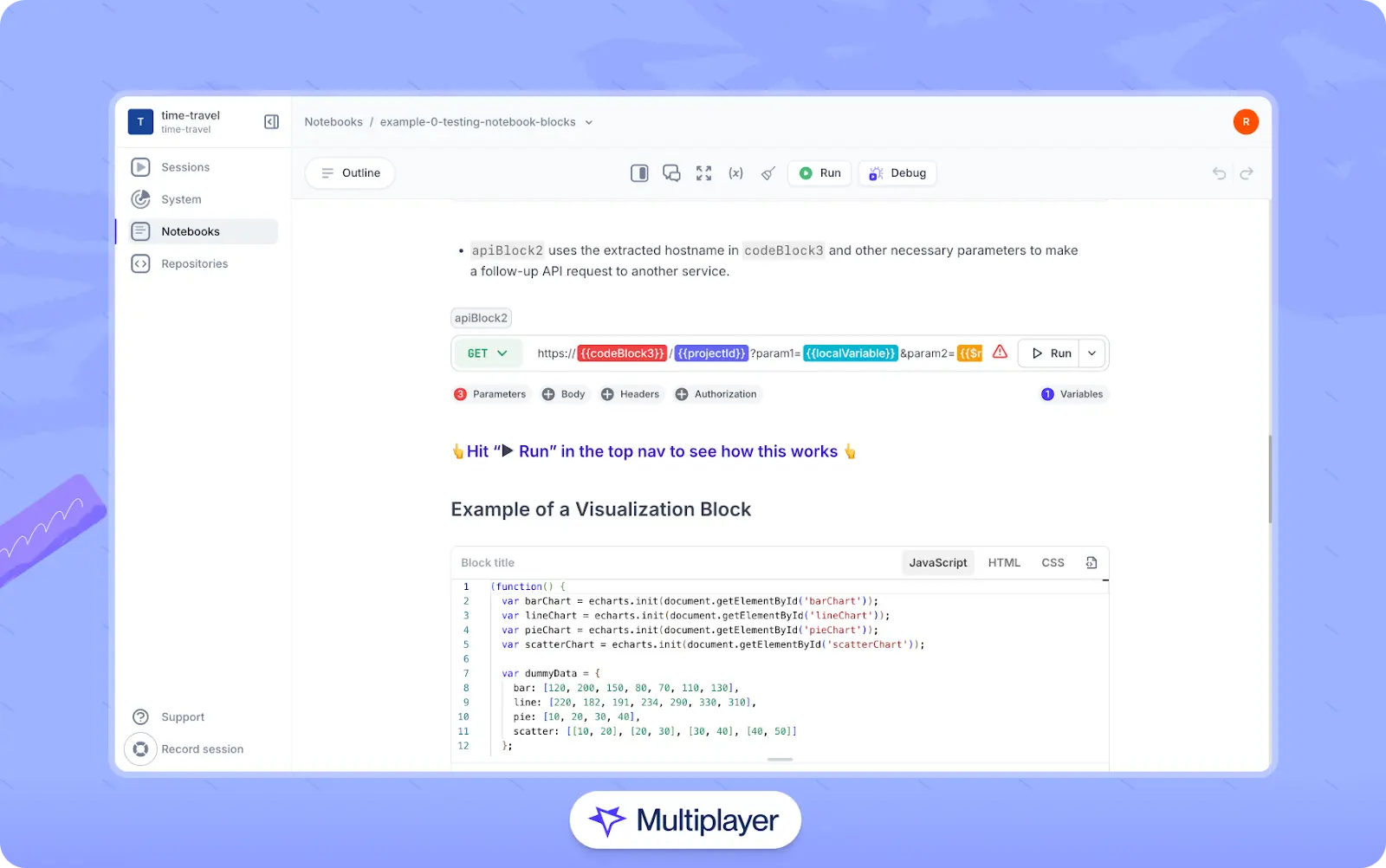
Multiplayer notebooks
Plan for scalability
A robust scalability plan requires careful planning and architectural design choices to support dynamic resource allocation and handle variable loads. SaaS developers can implement scalability in their platforms by selecting an optimal deployment model, keeping scalability at the forefront of system design decisions, and optimizing resource utilization.
Choosing the right deployment model
As discussed previously, common deployment models for SaaS architectures are full-stack silo, full-stack pool, and hybrid. Deployment models play a central role in balancing tenant isolation, performance, and resource efficiency. Each model comes with trade-offs that impact scalability and cost.
In the full-stack silo model, each tenant has dedicated resources, simplifying isolation and limiting the impact of failures, but this can become costly and difficult to scale with more tenants. The full-stack pool model, where tenants share resources, offers better cost efficiency but requires strong isolation mechanisms to prevent resource contention and security issues.
It is common for organizations to utilize hybrid deployments to achieve a practical balance between cost efficiency, scalability, and security. In a hybrid deployment, developers choose which services or subsystems to implement using either full-stack pool or full-stack silo.
When choosing a deployment model, it is most important to consider data and performance isolation requirements. Applications handling sensitive, high-stakes operations–e.g., financial platforms or healthcare systems–often favor the silo model for strict isolation, while content delivery or e-commerce platforms may rely more heavily on the pooled model for its cost efficiency. It is also important to consider compliance standards (e.g., GDPR, HIPAA) and which deployment models your team can implement to meet those requirements.
Designing the system for scalability
SaaS architectures must scale efficiently as user demand grows. Achieving this level of scalability requires thoughtful architectural choices that optimize resource usage and support growth without introducing inefficiencies. The techniques below can help SaaS systems achieve these goals.
- Stateless services: Stateless services treat each request as an independent transaction, unrelated to any previous requests. Because stateless services do not store persistent session data or rely on any specific instance to process requests, employing stateless services simplifies scaling, reduces session management complexity, and minimizes the risk of data inconsistencies.
- Asynchronous communication: Asynchronous communication patterns like message queues or event-driven designs enable microservices to operate independently. Decoupling services supports resilience and allows each service to scale as needed without creating side effects or cascading failures.
- Horizontally scalable data storage: Databases that support horizontal scaling help prevent bottlenecks as data volumes increase. Distributed databases like NoSQL or cloud-native databases can add nodes as needed, allowing storage and retrieval capabilities to grow with demand.
- Auto-scaling: Auto-scaling mechanisms dynamically adjust resources based on real-time demand to avoid over-provisioning during low-demand periods while ensuring sufficient capacity during traffic spikes. Auto-scaling is often achieved by using a cloud provider that provides configurable auto-scaling features to adjust usage based on predefined metrics.
- Caching: Caching strategies at various layers improve response times and reduce backend load, particularly if your application is read-heavy. Implement in-memory caches for frequently accessed data, CDNs for static assets, and distributed caches for data shared across instances.
One click. Full-stack visibility. All the data you need correlated in one session
RECORD A SESSION FOR FREEEmbracing continuous improvement
Maintaining scalability is a complex task. While an upfront investment in designing a scalable system is a good starting point, it is natural for a system to deviate from its original design due to evolving business requirements, tight development timelines, and other unforeseen circumstances.
These deviations can become critical issues when left unchecked. To avoid this scenario,teams must treat scalability as an ongoing practice. Regularly revisit architectural decisions, and be sure your team has a sufficient observability framework in place so that you have a current and historical view of metrics like latency, throughput, and resource utilization. If and when metrics begin to trend in undesirable directions, review recent deployments, configuration changes, and traffic patterns. If your organization has access to service-level dashboards, this can also be an effective way to quickly identify which components or endpoints are contributing most to architectural or performance issues.
Streamline testing and deployment
Effective testing and deployment strategies can speed up development, reduce errors, and ensure consistent functionality. In this section, we examine four effective practices that help realize these benefits.
Continuous integration and continuous delivery (CI/CD)
CI/CD pipelines allow teams to regularly integrate, test, and deploy new code without service disruption. In a CI/CD setup, code changes are continuously integrated, automatically tested, and prepared for deployment, helping to catch issues early and reduce deployment risks. Tools like Jenkins, GitLab CI, and CircleCI provide powerful automation that handles everything from code integration to deployment, improving team productivity and reducing time to market. Regularly deploying small, incremental updates ensures a stable production environment while enabling rapid feature releases.
Automated testing
Automated testing ensures that SaaS applications maintain high quality and reliability. Automated unit tests validate individual functions, integration tests check interactions between components, and UI tests ensure the application works as expected from the user’s perspective. Tools like Selenium for UI testing, JUnit for unit testing, and Postman for API testing allow developers to quickly identify and fix bugs, reducing the risk of human error. Implementing automated testing in CI/CD workflows accelerates release cycles while upholding product quality.
Feature flags
Feature flags (or feature toggles) allow features to be enabled or disabled independently of code deployments. They support agile updates without disrupting the entire tenant base.
- Targeted rollouts: Feature flags enable selective feature releases to specific user segments, such as beta testers or tenants in a particular region. This allows for controlled testing and feedback gathering before a feature is broadly available.
- Minimized blast radius: If a new feature introduces unexpected issues, the impact can be minimized by quickly disabling the feature flag, preventing the issue from affecting the entire user base. This aligns with the concept of limiting blast radius, a key consideration in SaaS environments, especially those using a full-stack pool model where an outage can have widespread consequences.
- Kill switches for rapid response: Feature flags can serve as “kill switches” to disable malfunctioning features immediately, preserving service stability and upholding SLAs without requiring a full deployment reversal.
A/B testing
A/B testing complements feature flags by enabling comparisons between feature variations to identify the most effective design for user engagement, conversion, or other key metrics. It also allows SaaS teams to run experiments with different feature versions that are exposed to specific user groups. By analyzing user responses and behavior, the team can determine the optimal version, refining the user experience and maximizing intended outcomes.
Visibility in debugging
When test cases fail or errors in a deployed environment are identified, debugging becomes a crucial practice. Outdated and inefficient debugging methods can incur significant costs and negatively impact the developer experience. Some examples of ineffective debugging practices include:
- Attempting to reproduce issues manually without sufficient context
- Adding temporary log statements throughout your codebase
- Relying on screenshots and anecdotal reports from users
- Troubleshooting within a local or staging environment that does not accurately reflect production conditions
These practices commonly miss key details and leave developers chasing symptoms, implementing patchy fixes, or painstakingly inferring context from scattered logs and APM dashboards.
A more structured workflow involves capturing end-to-end behavior for each failing scenario. This includes recording front-end screens and user actions correlated with backend traces, metrics, logs, and full request/response content and headers. Developers can use recordings to step through the exact sequence of events that led to a failure and inspect the variable states, payloads, and timing at each layer.
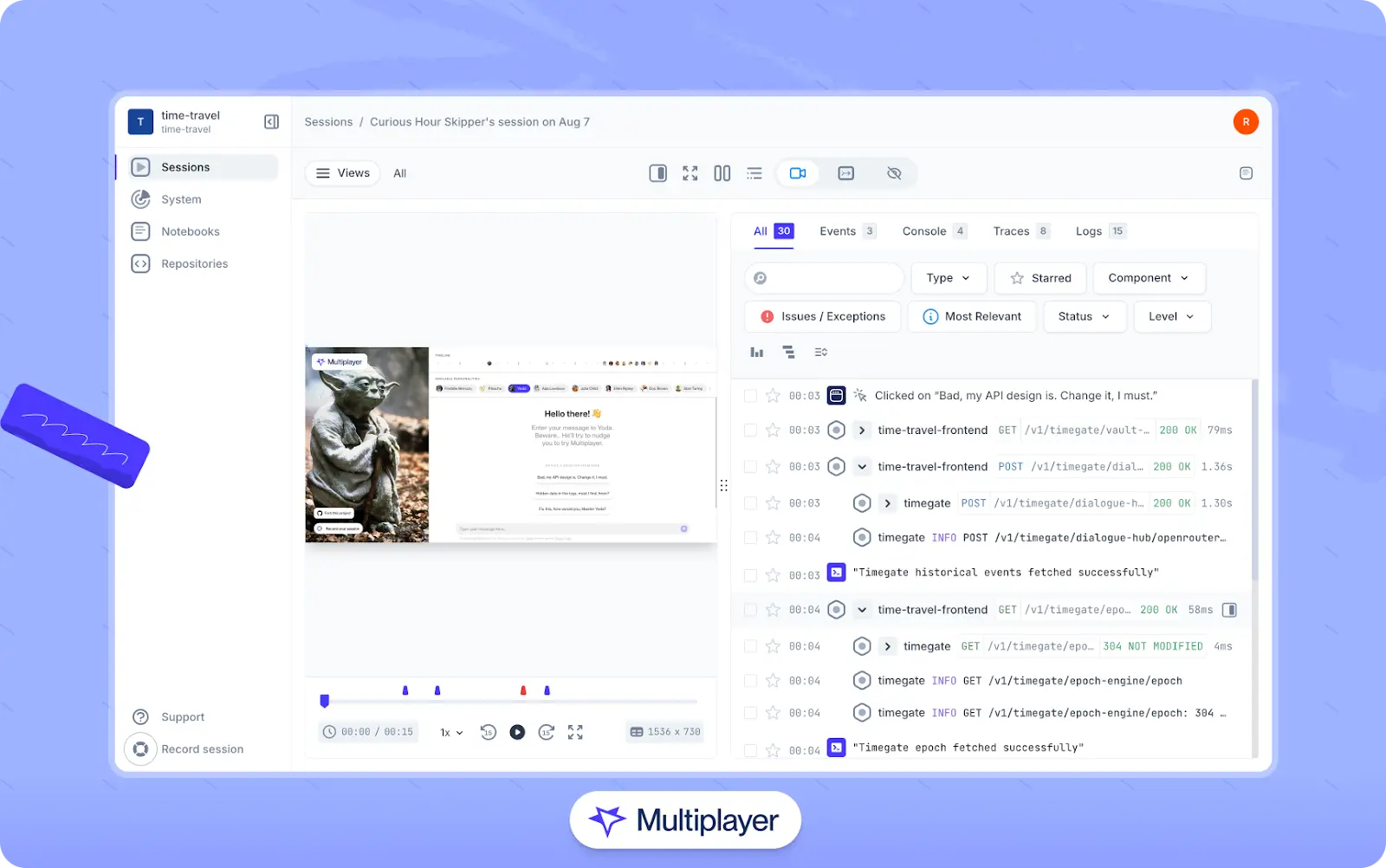
Multiplayer full stack session recordings
To integrate this into your workflow, follow the steps below:
- Instrument your system with an observability framework like OpenTelemetry to capture traces, logs, and metrics consistently across services.
- Route telemetry data to a tool like Multiplayer so that it can correlate frontend actions with backend activity.
- Replay and analyze failures step by step to identify where the system diverges from expected behavior.
- Analyze service configurations or application code to find the root cause. This can be done manually or by feeding session recording data to AI copilots or IDEs.
While no debugging workflow is foolproof, the approach above provides developers with a clearer picture of failures to help them diagnose and fix issues more reliably across the stack.
Employ modularity
Implementing modularity into any application enhances scalability, maintainability, and flexibility. Because SaaS applications are multi-tenant and continuously evolving, modularity is of particular importance in a SaaS architecture.
Starting simple
A gradual approach to modularity ensures a balanced trade-off between simplicity and scalability. For many startups or smaller SaaS projects, starting with a monolithic architecture provides a more straightforward initial development path. A centralized, monolithic codebase allows developers to focus on delivering core functionality without the overhead of managing distributed systems.
However, the desire to deliver features quickly should not overshadow sound design choices. Whether your organization foresees an eventual transition to a more modular architecture style or not, it is important to follow modular design principles throughout the monolithic codebase.
Ensure that each module has clearly defined business responsibilities and has access to the rules and data it needs without becoming overly dependent on other parts of the codebase. Map out each module’s responsibilities, data ownership, and dependencies in detail. Create thorough documentation that both assists in the current development process and indicates a potential pathway to a more modular architecture style down the line.
Teams should also implement monitoring and logging early to identify high-traffic areas, spot bottlenecks, and evaluate resource utilization. Doing so provides important telemetry data to help optimize the existing application and make better-informed decisions on which modules should be extracted into independent services.
Stop coaxing your copilot. Feed it correlated session data that’s enriched and AI-ready.
START FOR FREETransitioning to modular services
When components of the application reach the point where independent scaling, updates, or development becomes necessary, it is often advisable to start breaking modules into individual services. Use insights gained from monitoring and logging to identify modules that are highly utilized, create scalability bottlenecks, require strong security or data isolation, or have performance and latency issues.
From a development perspective, consider breaking out modules that are tightly coupled, require frequent updates, or consistently slow down development or deployments. The process of migrating to any new architecture style should be performed incrementally and only when adequate time and development talent are available. Prioritize changes based on business and development impact, and start with the most critical pieces of functionality.
Conclusion
Creating a successful SaaS application requires thoughtful planning, adherence to best practices, and a deep understanding of the challenges inherent to the SaaS model. The SaaS development techniques in this article can help engineers prioritize modularity, implement effective testing and deployment practices, design robust APIs, scale efficiently, and ensure security when developing SaaS applications. Following these guidelines will allow your team to deliver fast, reliable software that meets user needs and evolving business requirements.